Welcome to Week 3 of National Cyber Security Awareness Month. Reviewing what we have learned so far, Week 1 taught us to understand that anyone is at risk of a Cyber event happening to them. In Week 2, we put it into illustration as we explained how our footprint in the digital age has opened doors to threats we did not know we had.
This brings our journey into Week 3, where we explore The Reality Of The Risk of BEC, Phishing and Ransomware. While other threats such as data loss, privacy compromises and media liability events remain, all carriers report that BEC, Phishing and Ransomware events cause the most claims and the majority of losses in 2020.
Consider this information released just last week by Beazley, one of our valuable partners and a leading Cyber carrier:
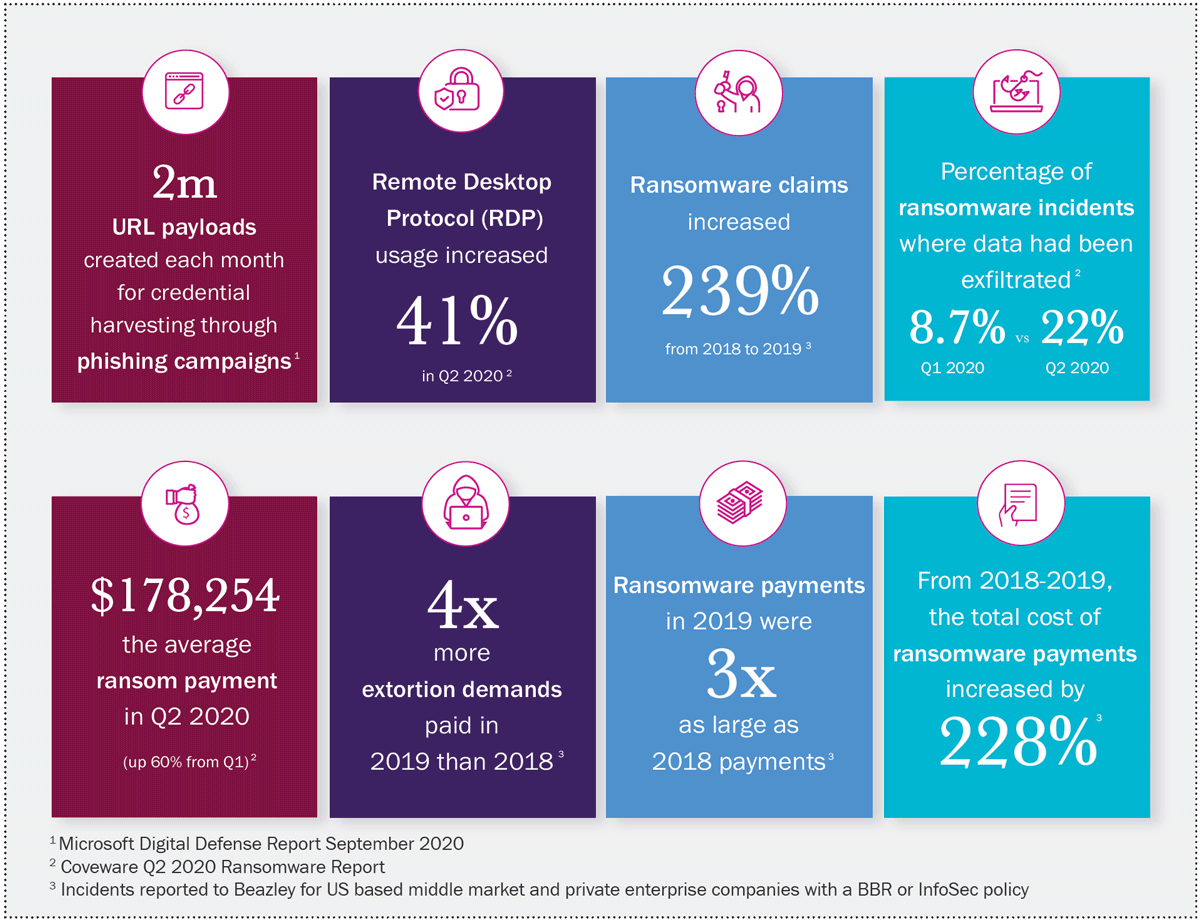
As you can see, a 239% increase in ransomware claims resulting 4 times the amount of extortions paid which were 3 times the size in a single year, from 2018 to 2019, leaving the average ransomware claim currently at $178,254. This will go up from 2019 to 2020.
In an effort to change our behavior patterns, which comes from education and training, we need to be first aware these events are increasing at an alarming rate, and next understand what they are and why they happen.
Here is a great example of how both Phishing and Ransomware campaigns work to effect an extortion event against your business:
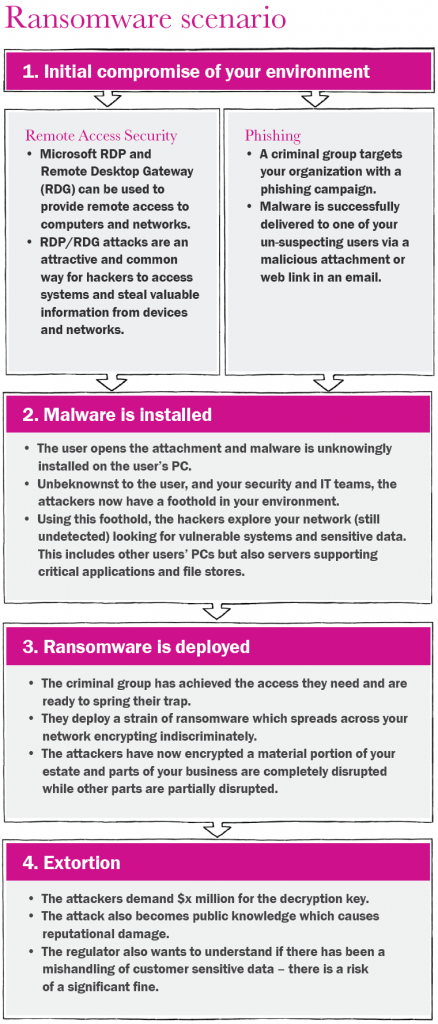
Since phishing relies on a third party to gain access to systems through only one employee, it is easy to understand why this is a successful method used by the Cyber criminal. As we have discussed in prior posts, human nature varies from person to person and this makes the learning curve for changing behaviors more difficult. Next week we will close out series on what you can do to make those changes happen.
Since phishing, and its cousin’s spear-phishing and whaling, proved to be so successful that the security industry and insurance carriers responded with social engineering training modules and self-directed phishing campaigns thus making these less effective, the Business Email Compromise (BEC) was born. The BEC has become even more dangerous because of its ability to masquerade as senior level people to steal large sums of money.
Here is a good explanation of what a BEC is and why it is used from WhatIs.com:
Business email compromise (BEC) is a security exploit in which the attacker targets an employee who has access to company funds and convinces the victim to transfer money into a bank account controlled by the attacker.
According to the FBI’s Internet Crime Report, BEC exploits were responsible for over $1.77 billion in losses in 2019. Business email compromise is one of the top cyber insurance claims in 2020, and security vendor Proofpoint has warned businesses that BEC exploits are increasingly being tied to COVID-19. The most common victims of BEC are companies that use wire transfers to send money to international clients.
BEC exploits often begin with the attacker using a social engineering scam to trick a C-level target into downloading malware, clicking on an infected link or visiting a compromised website. Once the C-level manager’s account has been compromised, it can be used to trick another employee into sending money to the attacker.
A popular BEC strategy is to send an official-looking email to someone in the company’s finance department. Typically, such an email will say there is a time-sensitive, confidential matter that requires payment be made to a customer’s, partner’s or supply chain partner’s bank account as soon as possible. The attacker hopes that the unsuspecting person in finance will think they are helping their company by facilitating a quick transfer of funds — when in reality, they are sending money to the attacker’s bank account.
There are numerous ways that BEC can be used to defraud targets. Here are a few examples:
- A compromised employee account requests a change in payee information and transfers payments to the perpetrator’s account.
- The attacker sends a bogus invoice to partner vendors in hopes they will pay the bill without questioning it.
- An attorney’s email identity might be used to pressure the target for immediate payment.
Cyber criminals may further use a compromised account (especially those of HR employees) to gain more personally-identifiable information (PII) for later use in defrauding the company or its clients.
We always tell our customers “Knowledge is information. Wisdom is what you do with it.” What I am trying to say is that the more you know, the better you can prepare and defend for what surely is coming your way. Next week’s in-depth discussion on how to change behavior patterns will close out this year’s National Cyber Security Awareness Month series, and provide you with some great tools to #BECYBERSMART.



















